Last month, we hosted a webinar with our partners at iProov, diving deep into the evolving landscape of multi-factor authentication. With phishing attacks becoming more complex and AI-powered fraud on the rise, old-school MFA approaches are showing their age.
Don’t miss the insights—watch the full webinar below to discover how to build stronger, more adaptable authentication strategies that protect your customers today and tomorrow.
[▶ Watch the Webinar]
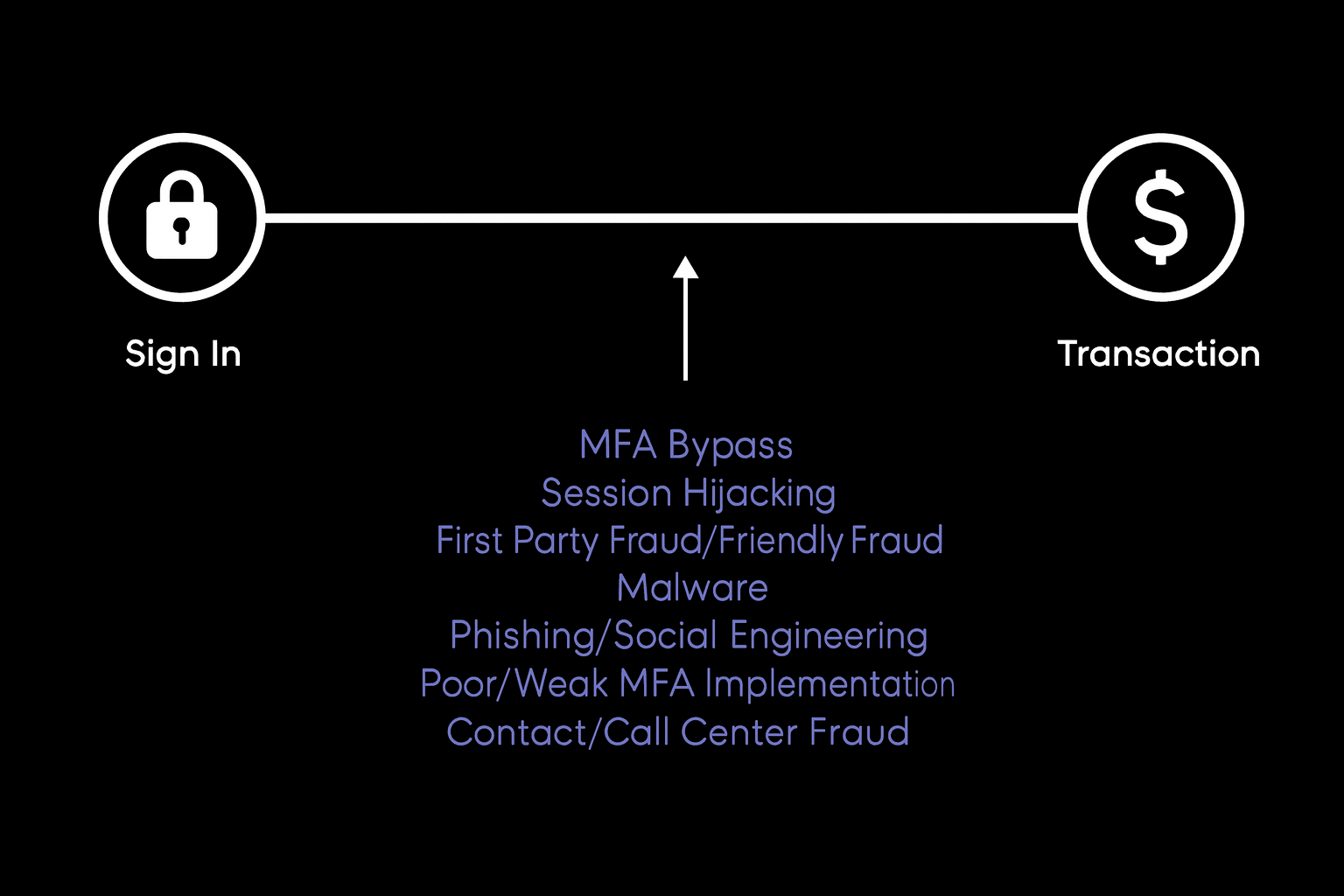
The problem with traditional MFA isn't just about your front door
Here's a misconception we hear all the time: "We've got MFA at login, so we're covered." But you just can’t lock your front door and leave every other entry point wide open.
Traditional MFA implementations typically focus on that single sign-in moment, but threats happen throughout the entire customer journey. Between your "front door" (login) and your customer's transaction, there are countless opportunities for bad actors to strike:
- Session hijacking - stealing active sessions from devices
- Phishing and social engineering - still the number one cybersecurity threat in 2024
- Contact center fraud - exploiting less secure workflows
- SMS man-in-the-middle attacks - intercepting those "secure" text messages
The reality is that authentication needs to be dynamic and journey-based, not just a one-time gate at the beginning.
The AI revolution is making attacks cheaper and more convincing
We've all seen the headlines about deepfakes, creating convincing fake content is no longer expensive or technically complex. Our colleagues at iProov demonstrated how you can perform a face swap attack for just $60 using a standard MacBook Air and readily available tools.
The data backs this up. iProov's threat intelligence shows:
- Face swap attacks surged by 300% in the last year
- The number of attack tools increased by 15%
- Many of these tools are now free or offer basic versions at no cost
- Image-to-video conversion tools can bypass even active liveness detection
What's concerning is the rise of "fraud as a service" - organized groups selling attack methods specifically designed to break KYC platforms used by banks and financial institutions.
Phishing-resistant passkeys
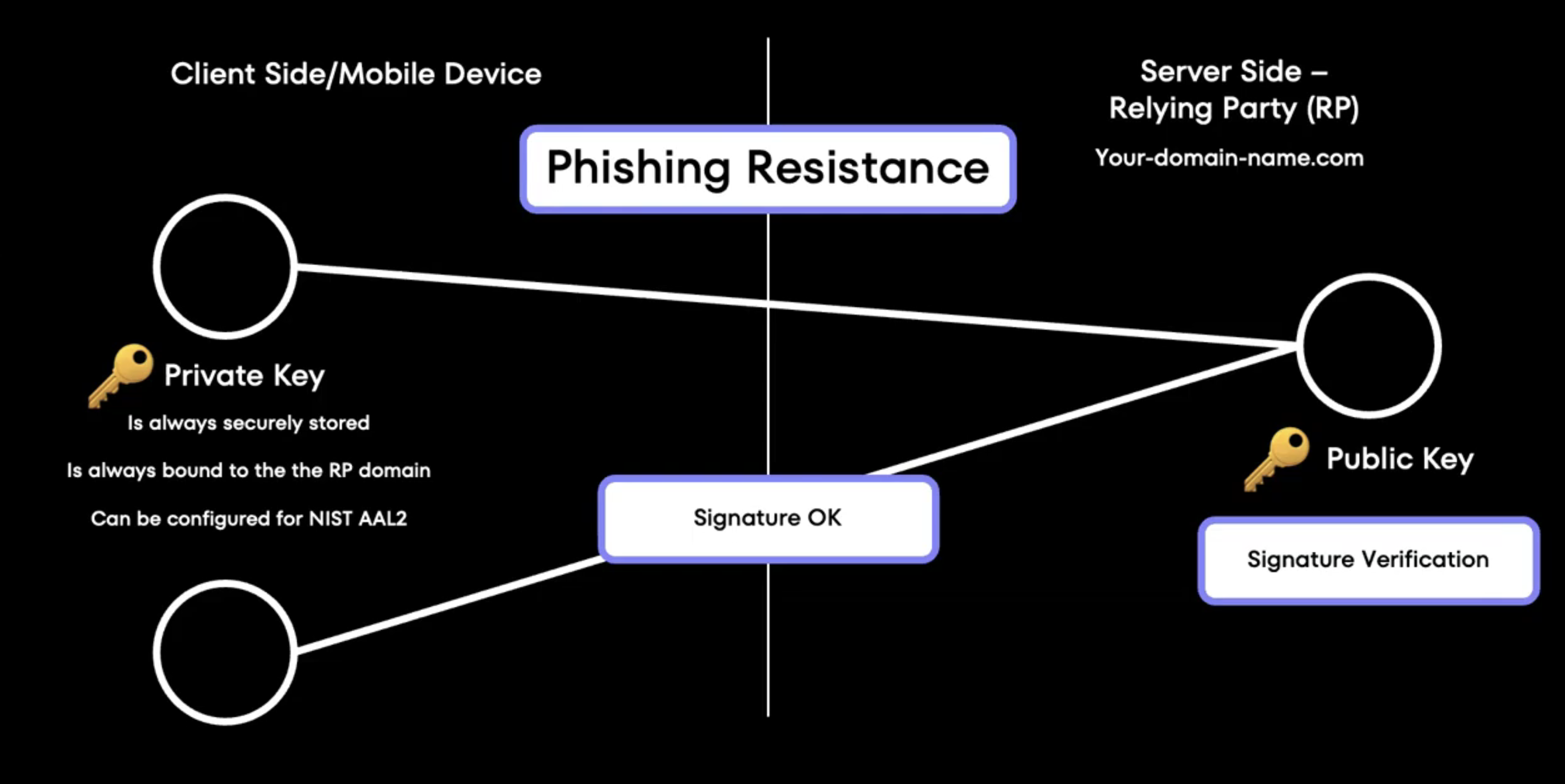
If there's one thing you take away from this post, let it be this: passkeys are phishing-resistant. That's their superpower.
Here's why passkeys are different from passwords or even traditional biometrics:
The cryptographic binding
Passkeys use a public-private key pair that's cryptographically bound to the specific website or domain that issued them. This means:
- You can only use a passkey on the legitimate website that created it
- Even if a phishing site looks identical to the real thing, your passkey simply won't work there
- The credential manager won't release the signature on fraudulent domains
Beyond screen lock security
Many banking apps today use what feels like biometrics - you open the app and use Touch ID or Face ID. But here's the key difference: that's just client-side authentication, essentially a fancy screen lock.
True passkey authentication involves end-to-end verification:
- Your device generates a cryptographic signature
- The server verifies this signature using the stored public key
- Both client and server participate in the security process
Biometrics are the perfect complement to passkeys
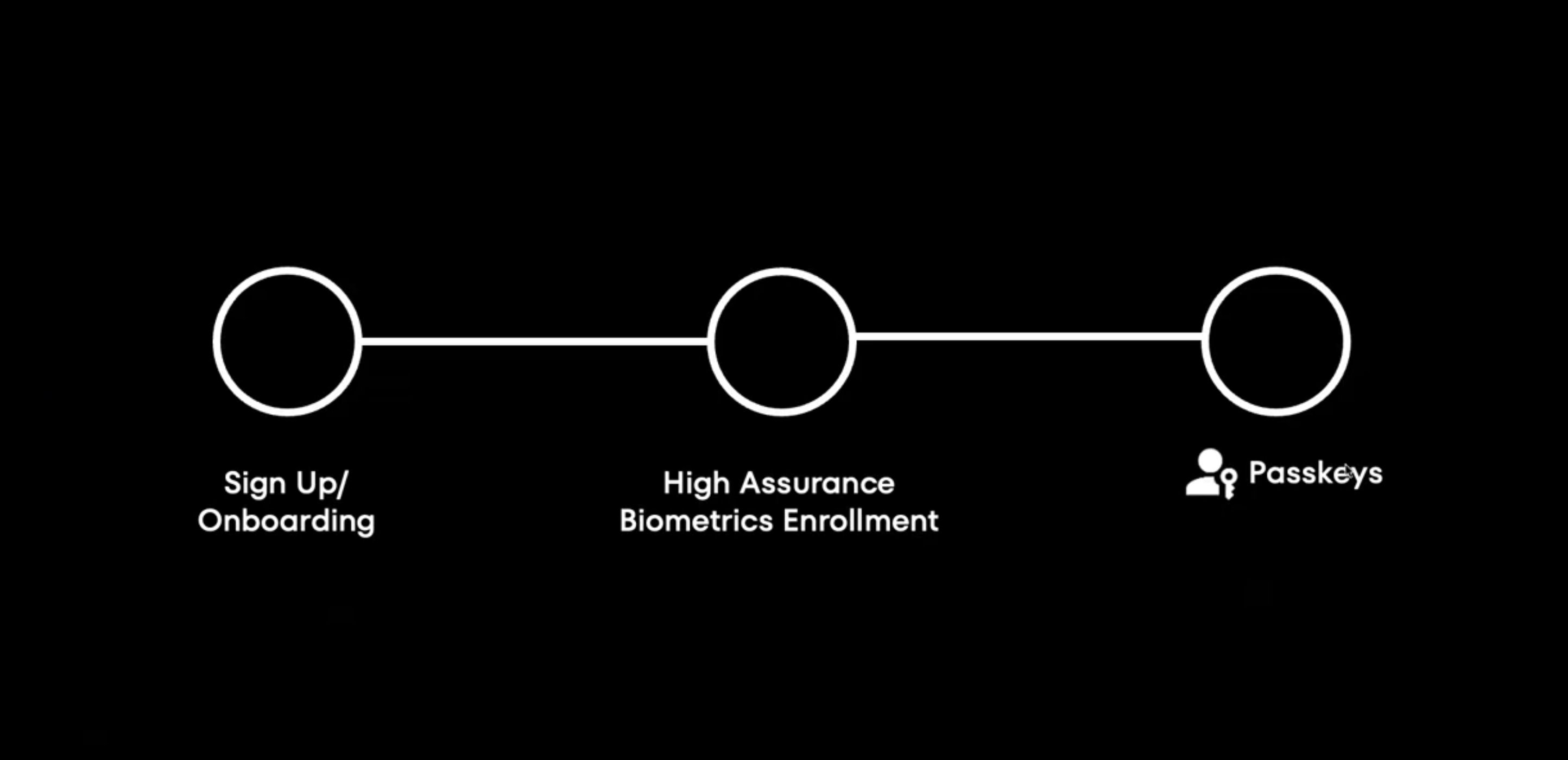
While passkeys prove possession of cryptographic material, biometrics answer a different question: "Is this really you?" When combined, they create what we call "inherent space authentication" - verifying who the user is, not just what they know or have.
Implementation points
The best place to introduce high-assurance biometrics is during onboarding, when the relationship with your customer is at its highest trust level. This is where you can:
- Bind facial biometrics to the user's identity
- Link biometrics to government-issued documents
- Create the passkey enrollment process
- Set up the foundation for risk-based authentication
Risk-based journey design
Not every transaction needs the same level of security. Smart authentication adapts based on context:
Low-risk scenarios: Simple passkey verification for small transactions to known accounts
High-risk scenarios: Biometric verification for:
- Large transactions above certain thresholds
- Transactions from dormant accounts
- Device changes or new device enrollment
- Account recovery situations
Real-world use cases where this actually matters
Account recovery
Traditional account recovery is often a nightmare - long waits, manual reviews, frustrated customers. With biometrics enrolled at account creation, users can recover access by proving they're the same person who opened the account, even if they've lost their device.
Dormant account reactivation
Banks spend enormous resources on manual re-KYC processes for dormant accounts. If you've already bound biometrics to the original KYC documents during onboarding, reactivation can be automated and instant.
Contact center authentication
Instead of relying on easily compromised knowledge-based authentication ("What's your mother's maiden name?"), agents can verify callers using the same biometric templates established during digital onboarding.
Regulation is catching up
For the first time in a while, regulation is actually keeping pace with technology. Central banks across the ASEAN region, including the Philippines, are actively directing financial institutions to move away from SMS OTPs.
This regulatory push is creating the perfect opportunity for banks to modernize their authentication infrastructure with passkeys and biometrics - not as a nice-to-have, but as a compliance necessity.
Getting started by thinking journey, not technology
When planning your authentication upgrade, resist the urge to think about individual technologies in isolation. Instead:
- Map your customer journey - identify all the touchpoints where authentication matters
- Assess risk at each stage - not every step needs maximum security
- Start with onboarding - this is your highest-assurance moment
- Design for recovery - plan how users will regain access when things go wrong
- Think holistically - combine passkeys and biometrics strategically
Your next steps
Authentication isn't just about keeping bad guys out, it's about creating experiences that don’t create friction legitimate customers while stopping fraud. The combination of phishing-resistant passkeys and high-assurance biometrics gives you the tools to do both.
The threat landscape is evolving rapidly, with AI making attacks cheaper and more convincing than ever. But the solutions are evolving too, and they're more accessible than you might think.
Start exploring how passkeys and biometrics can transform your authentication strategy. We're here to help you navigate this journey, from proof of concept to full production deployment.





.svg)
.png)