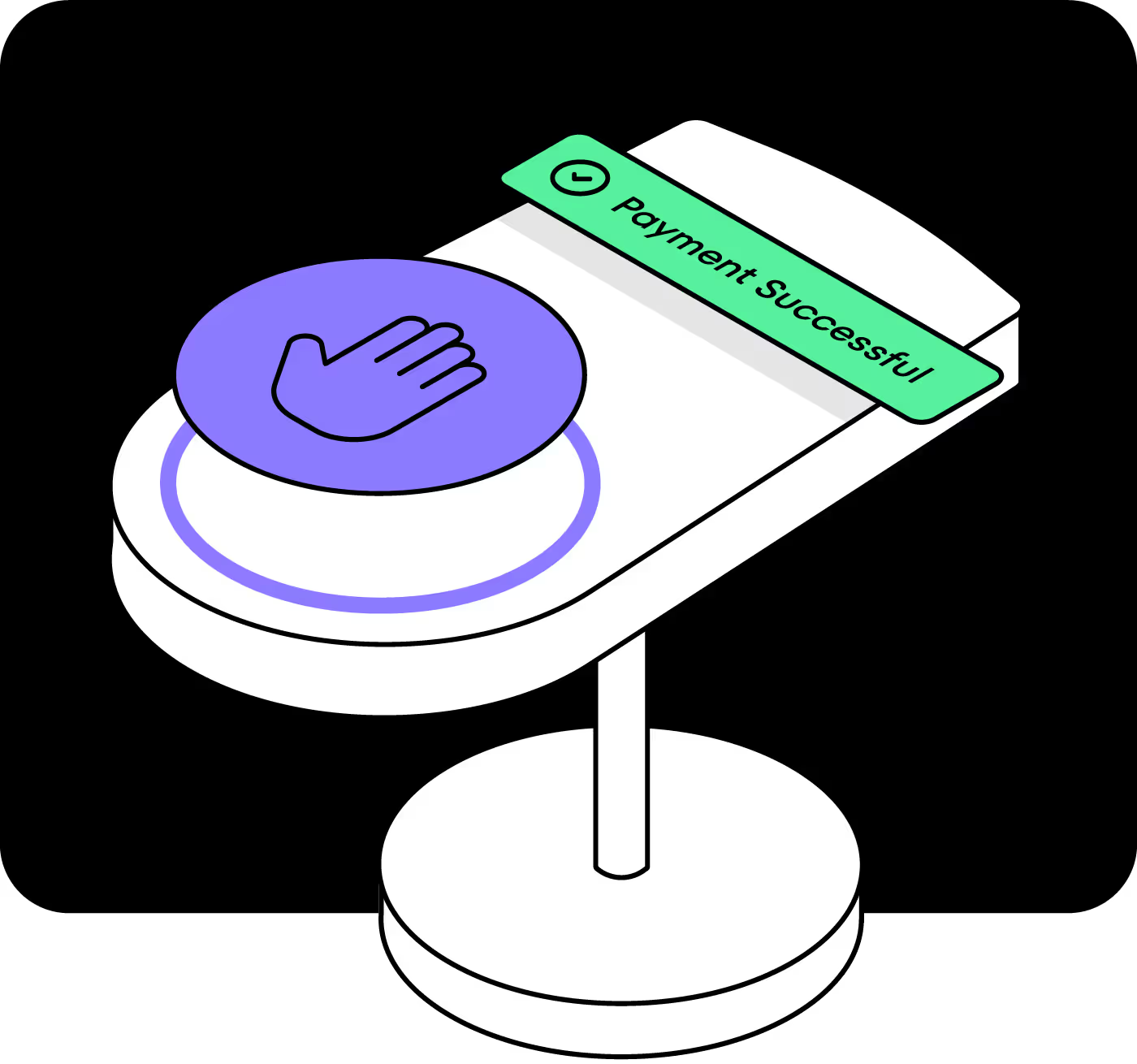
Palm vein biometric authentication uses unique vein and print patterns. Authorize payments, verify identity, and enable secure access and entry, all within the palm of your hand.

Fully brandable and themed for seamless enrollment and verification, delivering a cohesive experience.

Combines palm vein and palm print data to ensure unmatched precision in verification.

Hygienic and fast, ideal for environments requiring touchless interactions.
See palm biometric authentication in action with a live demonstration from NRF 2026, showcasing the world’s first palm-based crypto payment. This video highlights how palm biometrics can be used for real-world identity verification and payment authorization
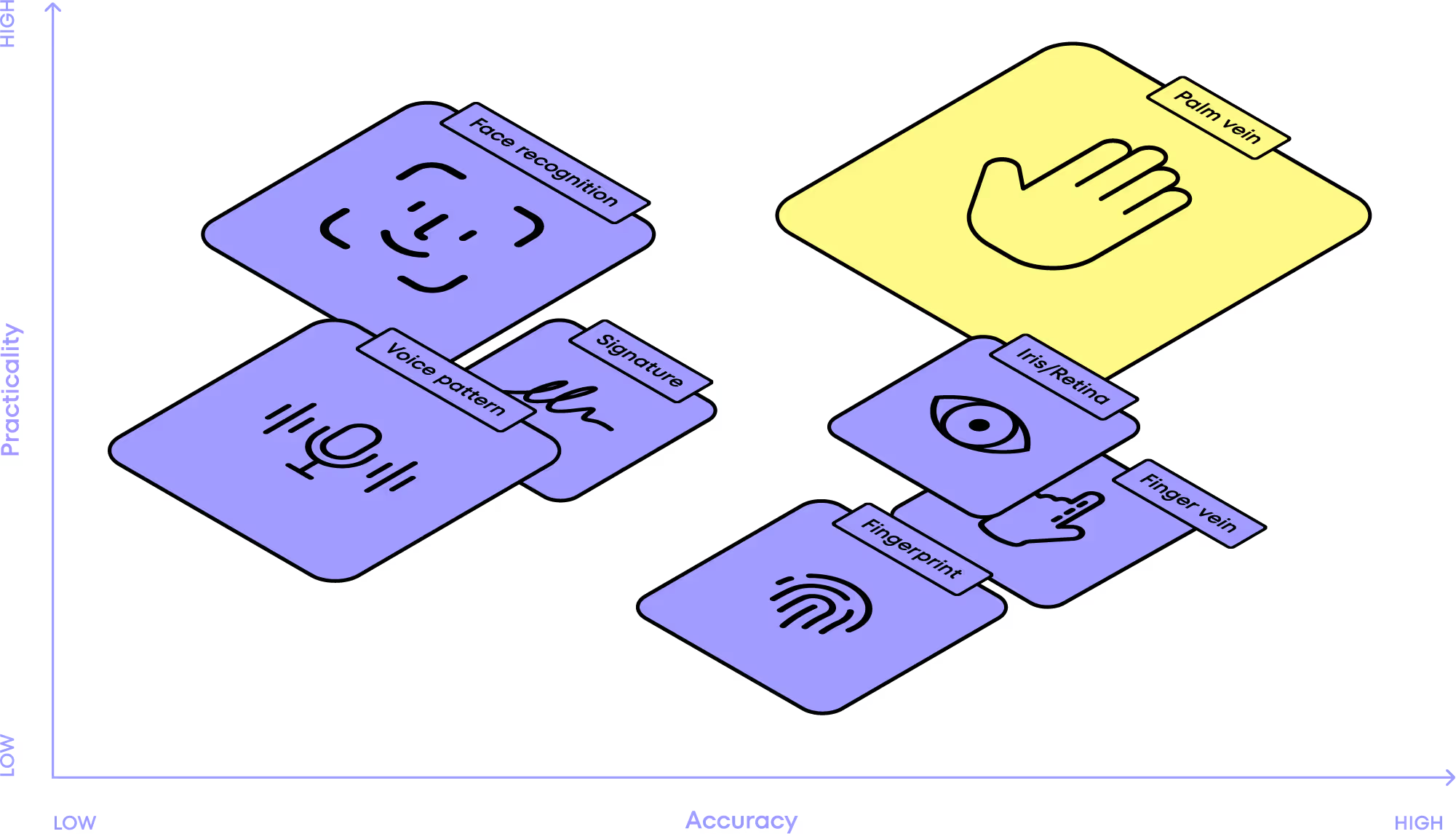
Palm scanning uses unique vein patterns in the hand for biometric identification. The scanner captures and compares these patterns to a database for secure authentication. It is also more practical and accurate than other biometric methods.

Deploy in retail and hospitality for fast, secure, and contactless payments.

Implemented in high-security facilities for secure, frictionless member or employee access.

Use at large-scale events for touchless authentication entry and age verification.

Enhances customer loyalty systems with biometric authentication tracking for personalized rewards.
Our partners

.avif)
How easy is it to integrate palm verification?
The IdX solution is built on the Authsignal platform, making it very simple to integrate; we call this last-mile integration. Integrators just need to fulfill integration at two critical points, enrollment, and delegated authorization (via webhook).
Do you need hardware?
Palm vein verification works optimally with specially calibrated infrared and RGB cameras, enabling the capture of both palm veins and prints. Authsignal’s fully integrated solution provides several Android-based device terminals from which to choose.
How does enrollment work?
The IdX terminal software solution supports a range of enrollment options, including Authsignal’s existing suite of passwordless authentication factors including in-app/QR code based signing, passkeys or you can bring your own enrollment (BYOE) mechanisms or flows, all programmatically driven.
Where can I review palm developer documentation?
What payment infrastructure does Authsignal support?
Authsignal's palm biometrics solution provides a white-label and customizable software platform that is agnostic of acquiring banks. Our software and hardware are purpose-built to integrate with your existing payment infrastructure to enable the rapid rollout of biometric payments.
Authsignal is your trusted partner for secure and compliant solutions, helping you protect data and earn customer trust every step of the way.






.avif)

.png)