Passkeys are making waves throughout the web, with large consumer applications (TikTok, Kayak) adopting passkeys as a way to streamline their customer's authentication experience but, more importantly, allow users to opt-in to an un-phishable and secure authentication factor.
There are a few implementation considerations before implementing passkeys, and we've broken them down for you here:
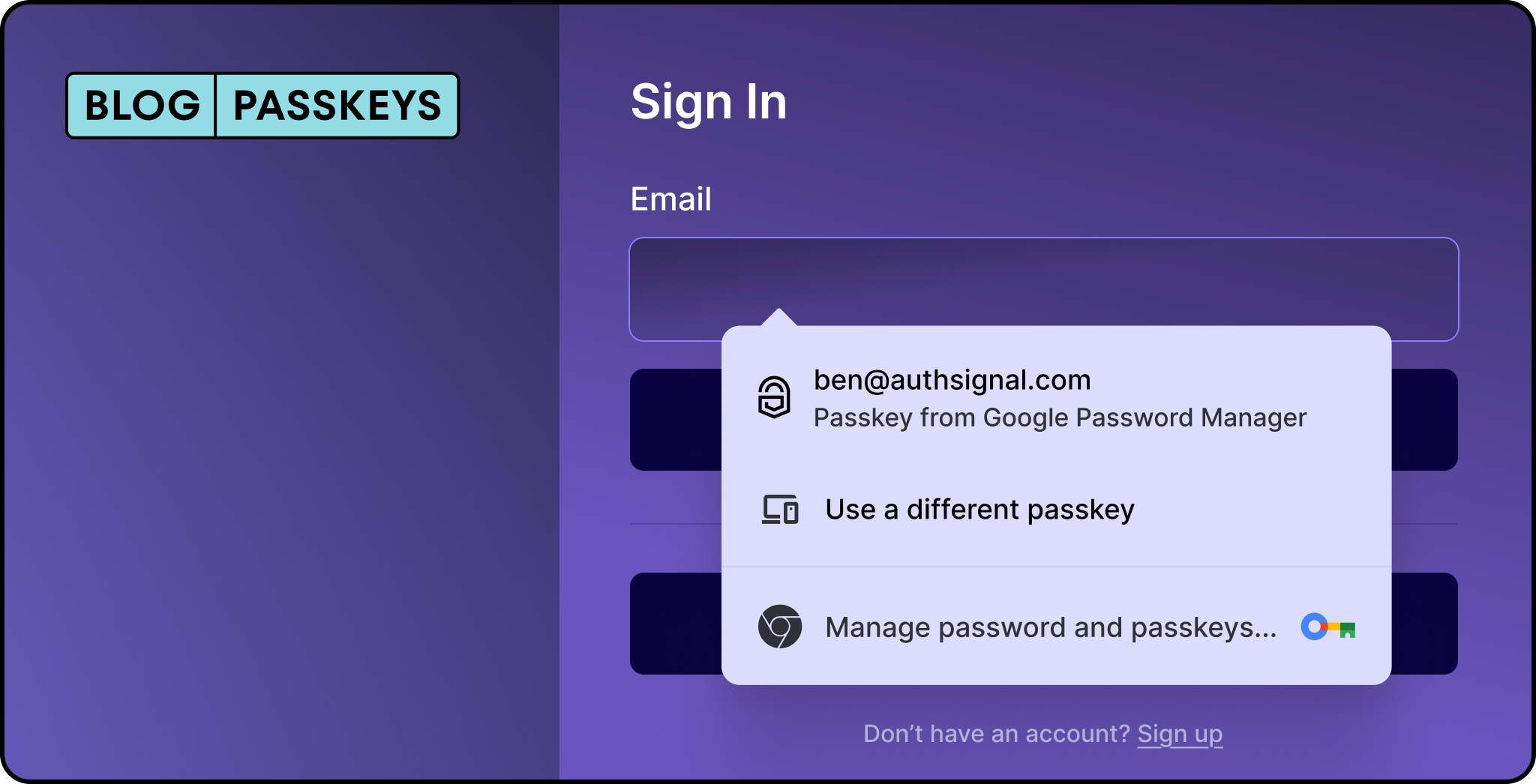
- How are your existing customers going to opt into passkeys?
- Which customer touch points and channels will you introduce passkeys on?
- What engineering expertise do you need in order to deploy and implement passkeys?
Ready to simplify passkey implementation? See how Authsignal’s APIs and SDKs can help your devs go live faster—with secure, scalable passkey-first authentication.
<blog-button>Book a demo<blog-button>
How are your existing customers going to opt-in to passkeys?
Educating customers on the benefits of passkeys is crucial in building adoption. And choosing the best place to prompt customers on enrolling into passkeys is important.
Ideally, passkeys should always be enrolled when the identity of the customer is highly trusted. This is mostly always at the point of a successful Two/Multi-Factor Authentication (MFA) step.
Allowing enrollment outside an MFA step creates a security risk because typical session or token-based mechanisms lose their assurance over time, as users leave laptops or phones unlocked or have devices with malware that can steal sessions/tokens. If there are no other mitigations placed, a bad actor can maliciously enroll their own keys, potentially locking your good customer out, thus reducing the effectiveness of passkeys.
With the combination of a compelling prompt to educate customers on the benefits of passkeys and a step directly part of a successful MFA challenge, this is the best practice to onboard a customer to use passkeys.

Using Authsignal's Hosted UI flows and client SDK's ensures that you'd be implementing Passkeys in the most secure way and offer best practice enrolment and opt-in flows. Authsignal also allows you to configure prompts through the no-code rules engine to target your rollout to specific users and specific points of their customer journeys.

Which customer touch points and channels will you introduce passkeys on?
Passkeys are a very versatile authentication factor that utilizes the WebAuthn APIs and FIDO2 standards. Passkeys can be used on many channels, including supported web browsers and native mobile devices.
Being able to deploy passkeys across all channels, both web and mobile, is the recommended approach, giving customers a ubiquitous experience whether they interact with your business on the web or the mobile device. Passkeys are being supported in more devices and browsers. For up-to-date passkey device support, check out this list here.

The most common touch point to allow passkeys is for Sign-in use cases because passkeys meet the definition of Multi-factor Authentication (MFA). You can use passkeys as the only authentication factor bypassing the need to use usernames and passwords or additional factors.
It's important to note that although this is the case, Passkey should still be considered as an alternative form of authentication as opposed to being a sole and primary authenticator. Giving your customers options will allow for more seamless account recovery processes.
The other use case and touch point you could use passkeys for is for step-up authentication and as a 2FA/MFA step. Passkeys are great not only on Sign-in but at critical points in your app. This could be placed just before your customer authorizes a high-value transaction or initiates a high-risk action.
We've provided an excellent Passkeys Demo site that demonstrates using passkeys both on Sign Up/Sign In and as a form of step-up within your customer experience.



.png)


.svg)