Proactively Stop Login Anomalies with Adaptive MFA.
Instantly detect and challenge login anomalies with Adaptive MFA, gain deep insights through advanced user observability, and ensure proactive security for user accounts.
<dark-button-outline>Create free account<dark-button-outline>


















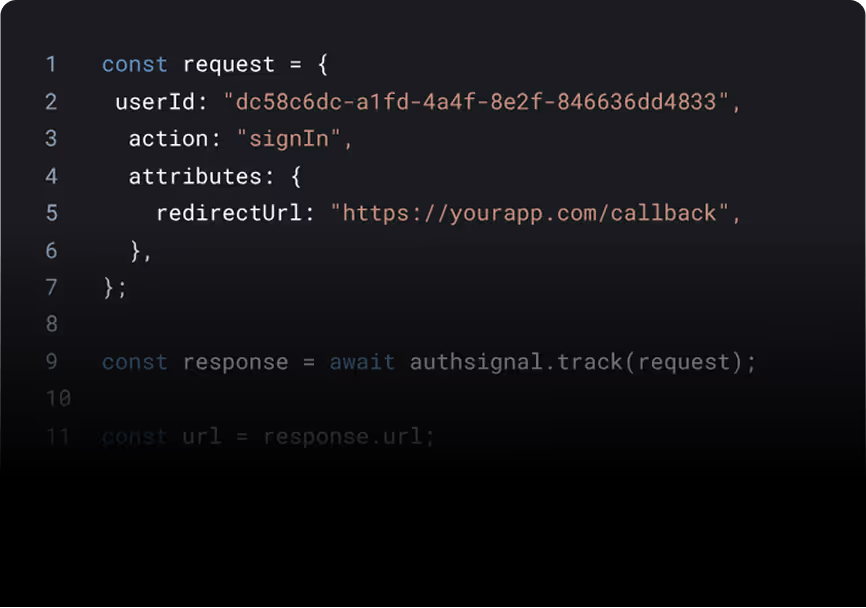
Fastest way to integrate MFA and Passkeys
Rapid deployment with pre-built UI, components, SDKs, and rules engine.
Unified authentication user experience
Combine passkeys, biometrics, and MFA into a seamless user experience.
Integrates with your Identity-Provider (IDP)
Integrate MFA and passkeys into any identity stack.
Implement best practices with expert support
Receive expert guidance and support to achieve top-tier passkey adoption rates.
Frequently asked questions
Can I export or import rules and policies?
Yes, Authsignal supports the export / import of rules. Additionally on our Enterprise plan terraform is available.
Does Authsignal support custom data points in rule and policy creation?
Yes, Authsignal supports custom data points in rule creation. Send custom attributes (e.g., user role, transaction amount, third party risk score, blockchain address) via API and use them in the rules engine to tailor authentication policies.

.png)